I recently presented at the Inside Azure management event. This event was packed full of Microsoft MVP’s and community experts from around the world. The focus on the event was around Azure Management based topics with some Kubernetes, AI, and DevOps topics sprinkled in.
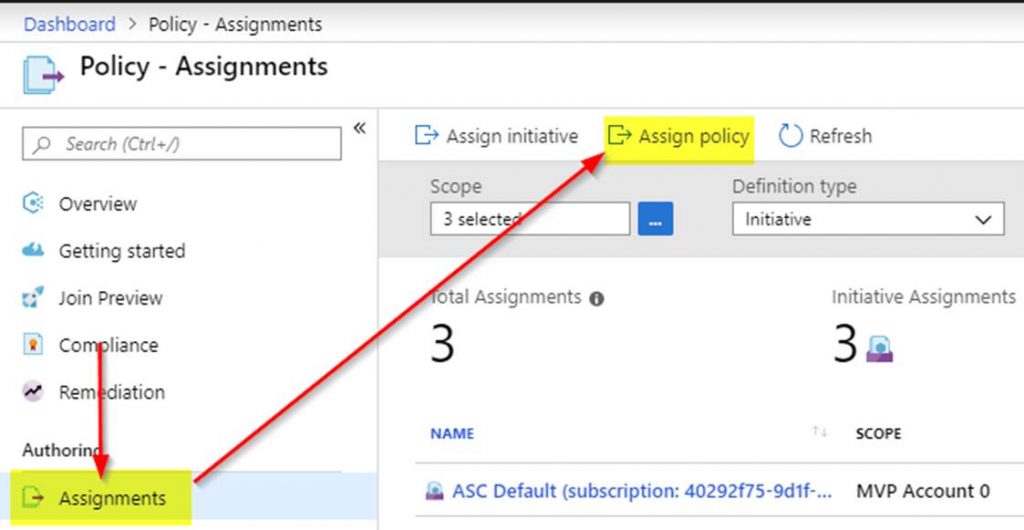
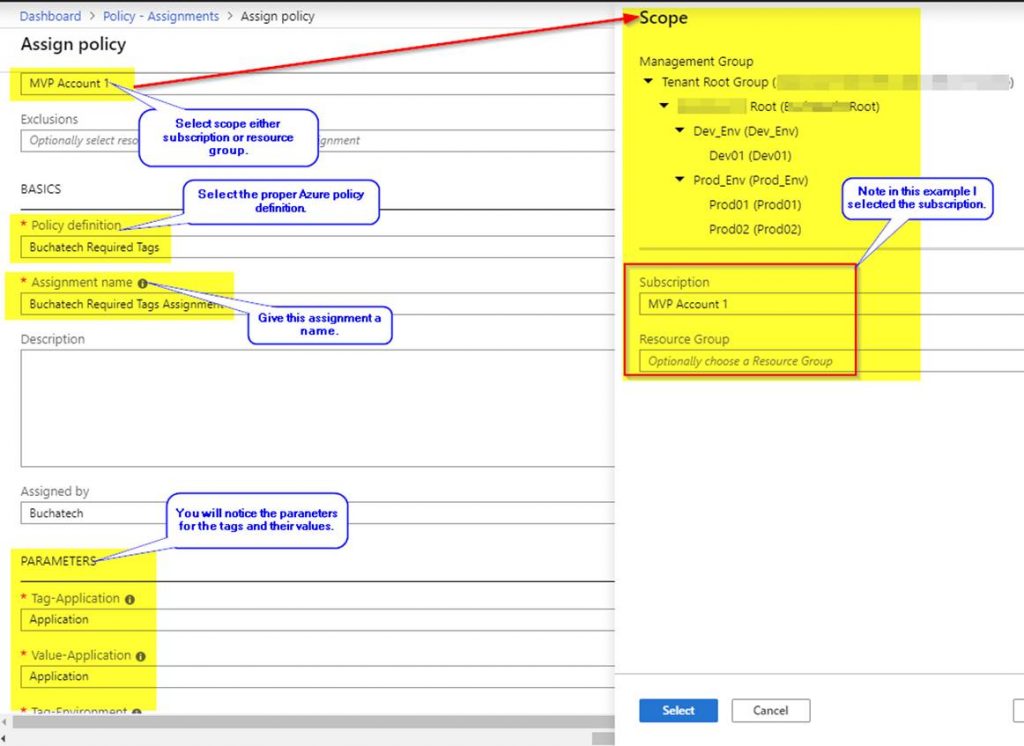
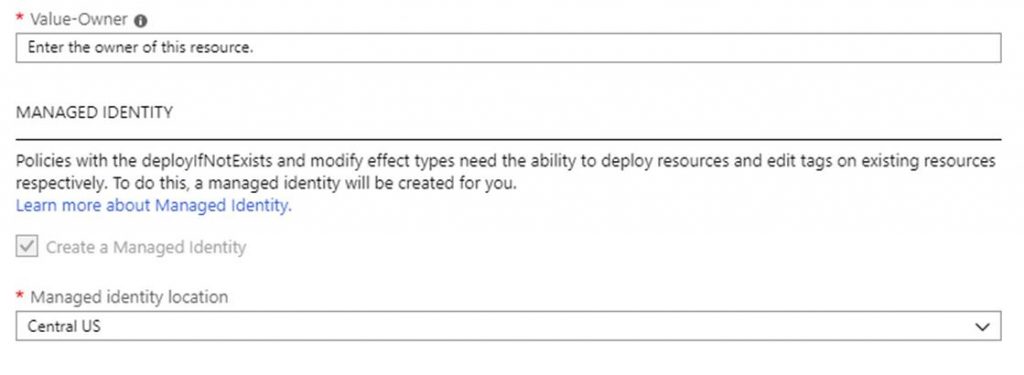
My session was “Azure Policy Insights & Multi-Tag demo via Azure Policy” Here is what it covered: “Azure Policy is a great tool when it comes to auditing and ensuring your cloud governance is met. In this session 9 time Microsoft Azure MVP Steve Buchanan is going to take you on a full-speed ride on the ins and outs of Azure Policy and land you with a recipe for handling a multi-tagging strategy with Azure Policy. Some of the key topics you will learn from this session include:
- Overview of Azure Policy
- Azure Policy Configuration best practices to meet compliance (NIST, PCI, ISO, HIPPA)
- Securing Azure services: AKS / Networking / SQL / App Service
- Azure Policy vs RBAC
- Overview of Azure Policy Guest Configuration
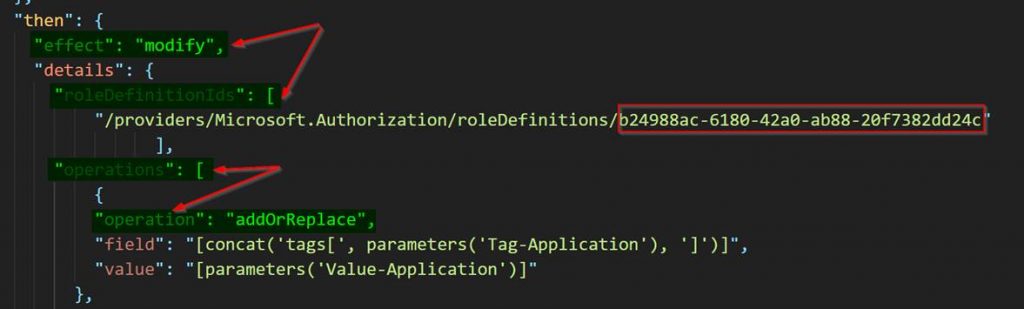
- Tagging and more“
The event has passed and if you didn’t make it no worries! All of the sessions have been recorded and uploaded to the Inside Azure management YouTube channel to be watched at your leisure. Here is the link to the YouTube channel where you can watch all the sessions:
The event coordinators have also set up some Youtube playlists to make it easier to find videos on the topics that pertain to you. They broke these out in the following categories: Azure Management, Artificial Intelligence in Azure, Cloud Governance, Cybersecurity, and DevOps.
You can watch my session right here:
Also here is the direct link to the video of my session on YouTube: https://youtu.be/EfAiITcExK0
Thanks for checking out my session and others from this event. Stay tuned to my blog for info on where I will be speaking next!