Another critical part of managing any cloud is security. In Azure Microsoft has a service called Security Center. I am going to cover Security Center at a high level here in this post as Security Center itself is a big topic and is frequently changing with new improvements. This provides continuous assessment of your clouds security posture. Security Center gives you a central place to monitor and manage your security. Security Center can even covers Hybrid Cloud with the ability to extend on-premises. With Security Center you can apply security policies to your cloud workloads and respond to attacks that occur.
Security Center has a “free” tier that can be used with any Azure subscription. In fact if you are running Azure you should at a minimum be utilizing the free tier of Security Center. The tiers are:
Not covered = not monitored by Security Center.
Basic Coverage = subscriptions under this “free” tier are under the limited, free level of Security Center.
Standard Coverage = subscriptions under this “standard” tier have the maximum level coverage by Security Center.
Key features in Security Center are:
– Security policy, assessment, and recommendations / free / Security Center performs continuous assessment and recommendations based on security policies that are set. This is the core feature of Security Center.
– Event collection and search / standard / Security Center can store security events in a Log Analytics (LA) workspace. The events also are available in the LA workspace for searching.
– Threat Protection / standard / visibility into any detected security alerts and their severity level.
– Just in time VM access / standard / Just in time VM access locks down inbound traffic to IaaS VM’s. With this feature users are required to request access to the VM for a specified amount of time. A firewall rule is opened on an NSG allowing the access and then the ports are closed after the allotted window of access time. This can reduce the attack surface on VM’s.
NOTE: (Automate Just In Time VM Access Request With PowerShell – https://github.com/CharbelNemnom/Power-MVP-Elite/tree/master/Request%20JIT%20VM%20Access by Microsoft MVP Charbel Nemnom)
– Adaptive application controls / standard / This feature allows you to choose what applications are allowed to run on your VMs. This feature uses machine learning to analyze the applications running in the VM and then you whitelist the ones you want to allow to run.
– Custom alerts / standard / Security Center has a bunch of default alerts. Alerts fire when a threat, or suspicious activity occurs. You can find the list of the default alerts here: security alerts. Security Center also has custom alerts that you can setup. With these you define the conditions upon which an alert is fired.
– Threat intelligence / standard / this feature watches for known bad actors using threat intelligence data from Microsoft’s global products and services such as Azure, Office 365, Microsoft CRM online, Microsoft Dynamics AX, outlook.com, MSN.com, and Microsoft’s Digital Crimes Unit (DCU) and Microsoft Security Response Center (MSRC) .
It is important to note that Security Center leverages many other Azure services to power its services. Some of these other Azure services include:
- Azure Policy
- Log Analytics
- Logic Apps
- Machine Learning
Now that we looked at key features of Security Center let’s take a tour of Security Center. The best way to navigate Security Center is via the navigation on the left hand side and that is the way I will break it down. The menu sections are shown in the following table:
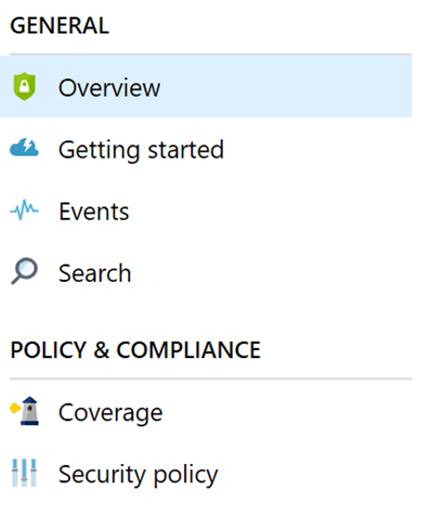 |
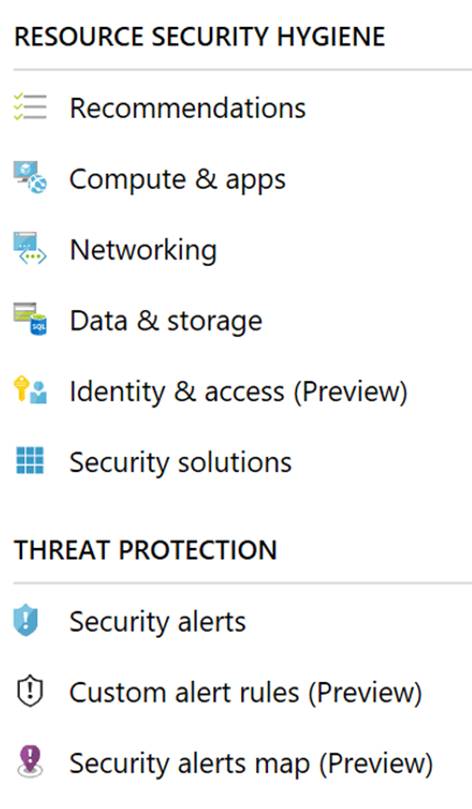 |
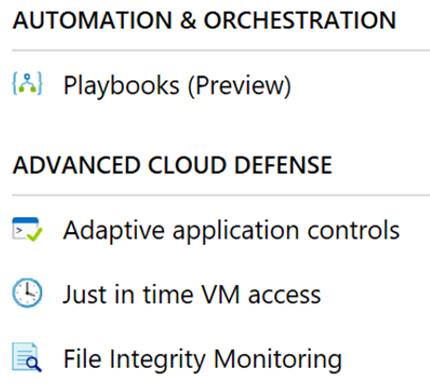 |
When you first click into Security Center you will see the Overview. Overview is also the first section under “General”. Here is a screenshot of the overview pain.
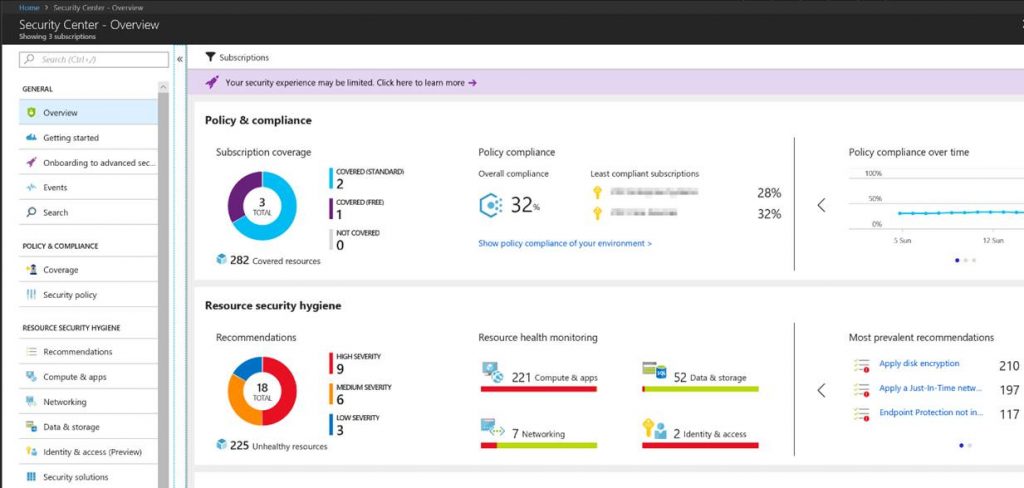
Essentially the overview pane gives you a summary of your security posture pulling in data from several sections in Security Center. Getting started is where you can launch a 60 day trial on the standard plan. Events brings you to a log analytics workspace dashboard to give you another display and search capabilities on your security data. Search will bring you directly to the log analytics search screen where you can search on your security data.
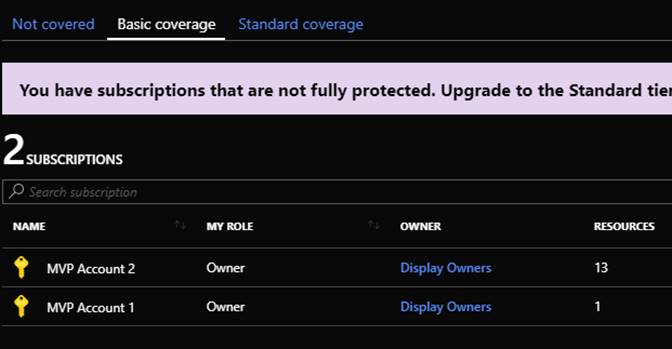
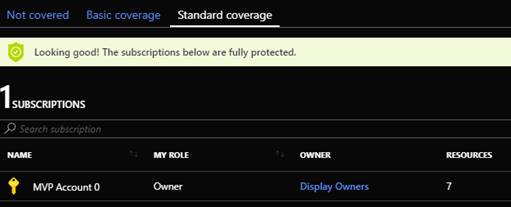
“Policy & Compliance” essentially gives you insight into security state and compliance across your subscriptions. Coverage will show you what level your subscriptions are covered at. This is shown in the following screenshot.
| Showing subscriptions under Basic coverage | Showing subscriptions under Standard Coverage |
|
 |
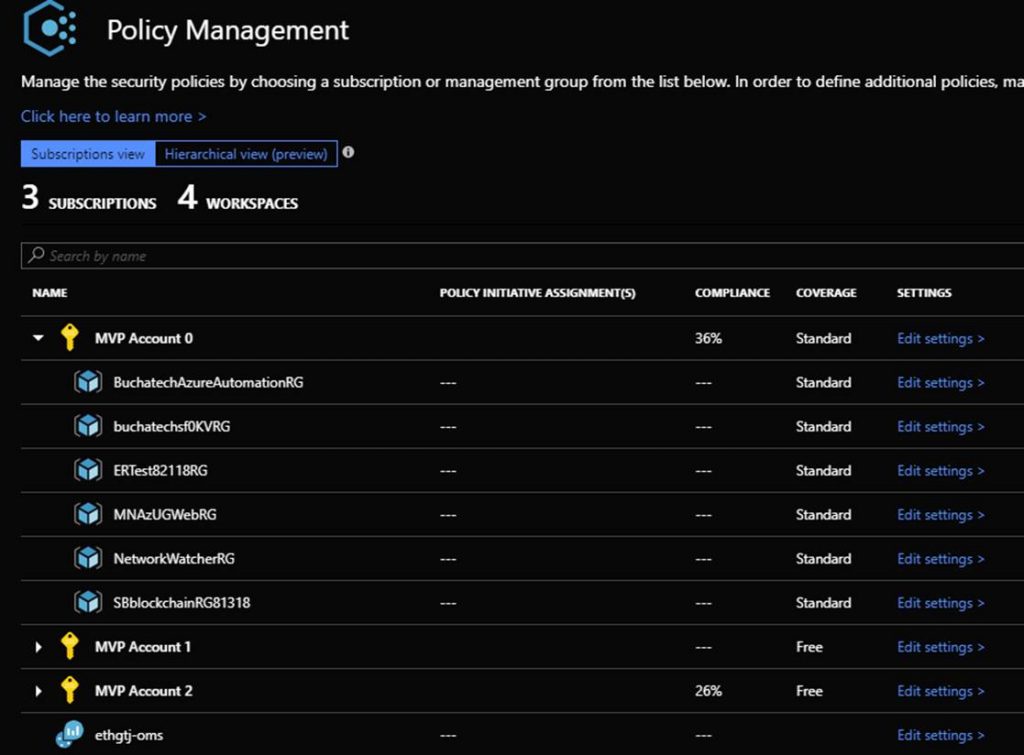
Security policy is where you can see your subscriptions and modify the settings and security policies turned on for them. To access the settings click on Edit Settings.
This is the settings screen:
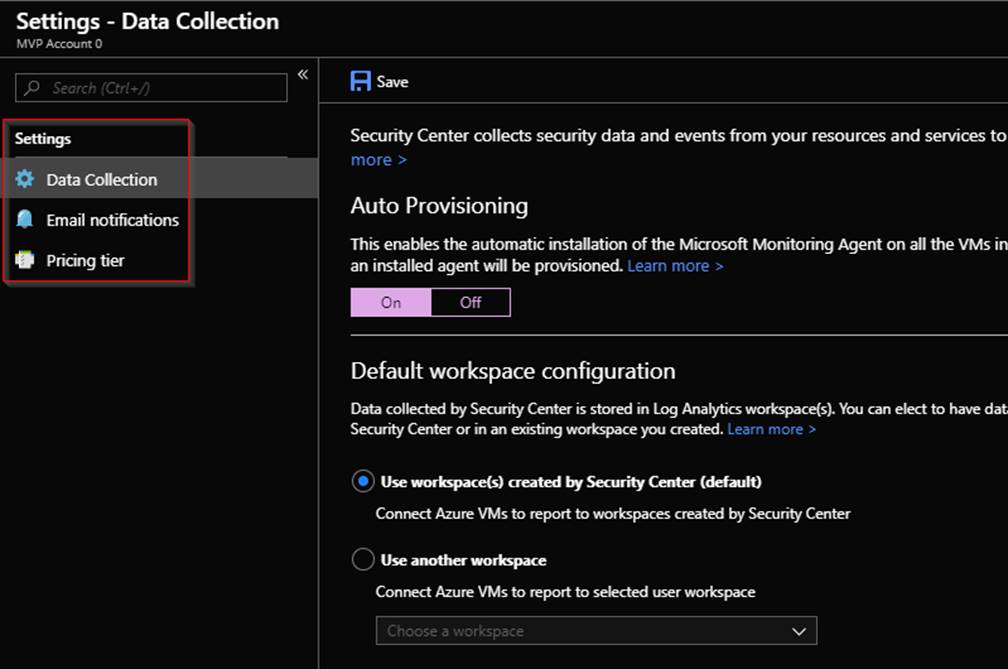
In the Settings screen you can modify your data collection and Log Analytics workspace data is sent to. You can set the email address and notification settings along with the pricing tier. To access the security polices click on the subscription itself and you will go to the security policy screen. This is where you can turn off or on what policies you want security center to continually assess for. This is shown in the following screenshot.
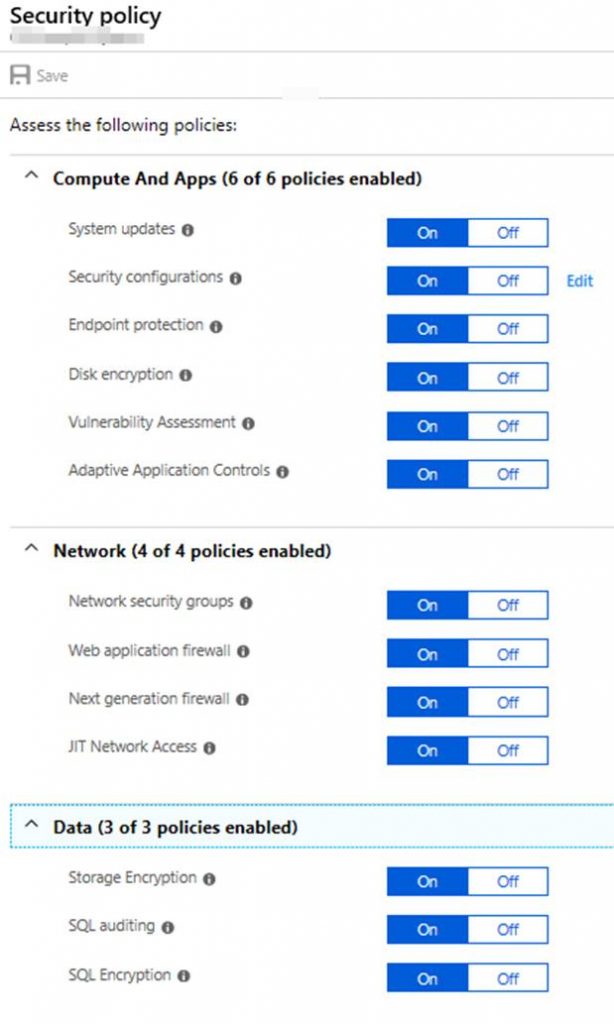
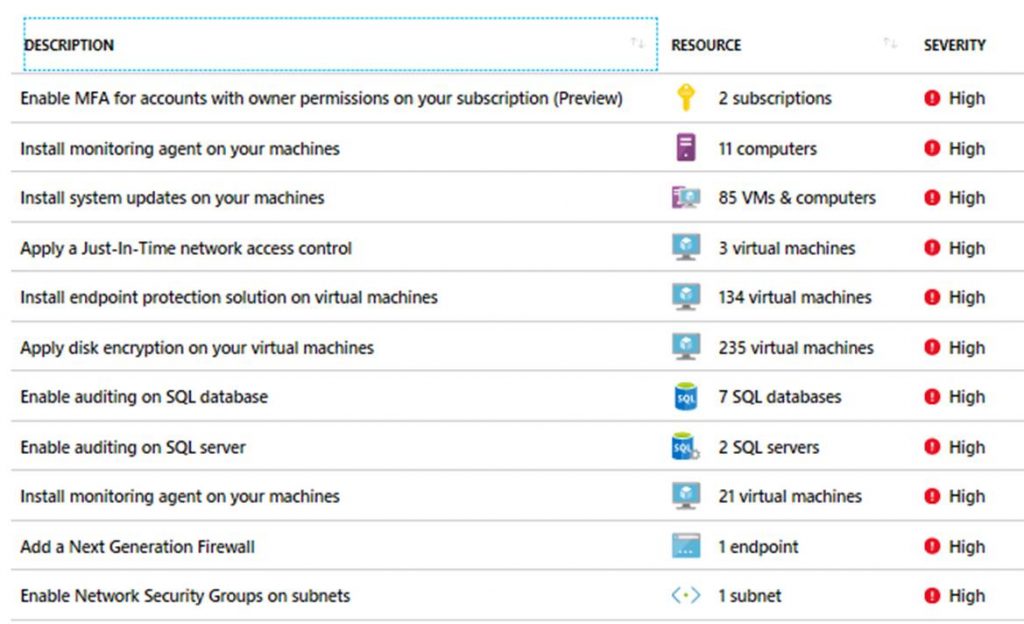
“Resource Security Hygiene” gives you information on your security state across cloud or hybrid-cloud workloads. The state includes recommendations and resource health monitoring. Recommendations gives you a summary recommendations across all of your cloud resources as shown in the following screenshot.
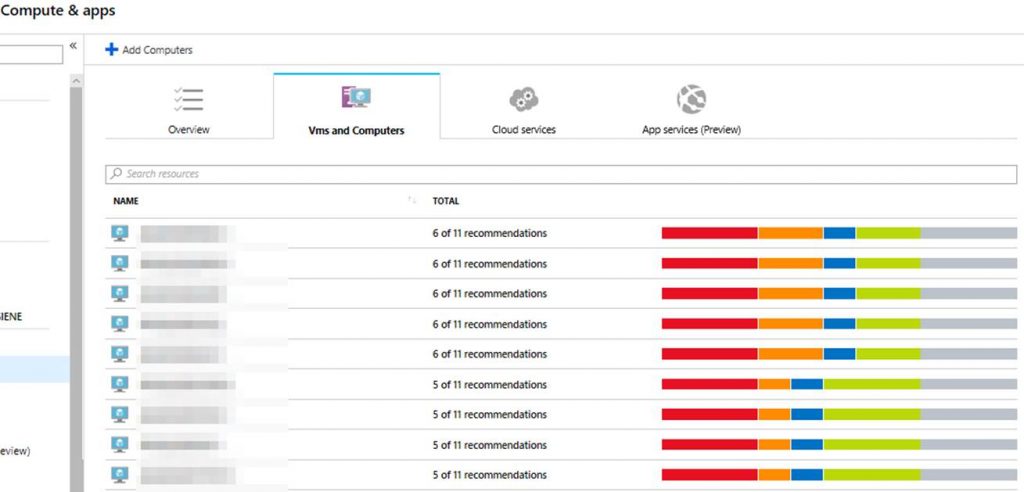
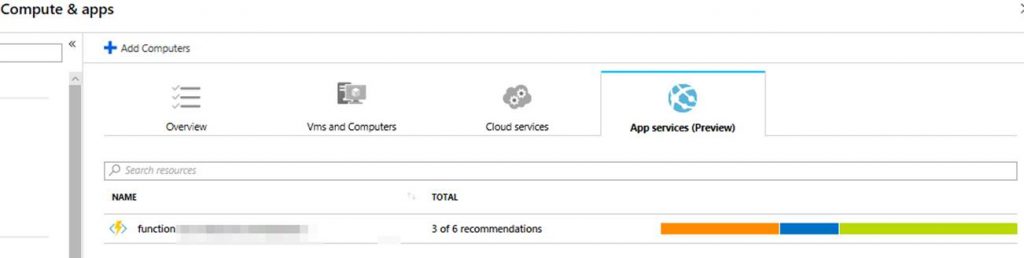
The other sections under Resource Security Hygiene give you security state data scoped to specific workload types. The current workload types are Compute & apps, Networking, Data & storage, and Identity & access. Here are some examples of what you will see in these sections.
Security solutions is where you can integrate 3rd party security solutions such as endpoint protection, next generation firewalls and more.
“Threat Protection” automatically collects security data from your Azure workloads, your Azure network, and partner solutions. This security data is used for adaptive protections powered by machine learning. Threat protection has security alerts, an alert map powered by Log Analytics, and where you can configure custom security alerts.
“Automation and Orchestration” Contains Playbooks. Playbooks in security center are still in preview at the time of this blog post. Playbooks are Logic Apps. Playbooks can be triggered from a security alert as a response to a threat. Learn more about the Playbooks and Logic Apps here: Security Playbook
“Advanced Cloud Defense” essentially is a bundle of advanced tooling that helps you defend your Azure resources proactively reducing threats and your attack surface. Within Advanced Cloud Defense you have Adaptive application controls, Just in time VM access, and File Integrity Monitoring. Adaptive application controls allows you to whitelist applications that are allowed to run on your VMs. Just in time VM access lets you lock down inbound traffic to Azure VM’s complete with a request process. File Integrity Monitoring is used to monitor changes to files. It validates file integrity for changes that might indicate an attack. This is powered by Log Analytics.
The last thing I want to call out is that Security Center can be integrated with external SIEM solutions. The following in a screenshot of the workflow that is used to get data from Security Center to a SIEM solution.
 |
| Image from Azure portal |
Currently supported SIEM’s are:
- IBM Qradar
- Splunk
- SumoLogic
- Any Syslog server
That wraps up this Security Center blog post in my Azure governance and management series. Again this is just scratching the surface on Security Center and it is being enhanced by Microsoft all the time. It is best to spin up Security Center in the Azure portal and check it out first hand.


1 thought on “Cloud Security via Security Center”