This blog is for those that have your Exchange stores and logs on the C drive and the c drive on your server is running out of space. You know you need to move them but you don’t know how. Well I will cover this in this blog step by step below.
NOTE: Here are a couple of things to note before going further:
- If your server is running out of space on the C drive check all possible areas and be sure Exchange is the culprit before moving its components around.
- Do not jump on the server and start manually deleting log files.
- This post is to be used before your disk is full or after you have recovered from a full disk disaster. If your disk is completely full now visit this link How to Recover from “Disk Full” on an Exchange Log Drive once you have cleared some space come back to this blog to move the log files and database store.
- Make sure you have a good backup of Exchange before following these steps.
- Use the below steps at your own risk.
MOVING THE DATABASE:
First off we are going to use the Move wizards in this post for both the logs and databases move. Using the wizards will simplify these tasks and we like to keep things simple. If you would prefer to do this in PowerShell see the link at the end of this blog post.
- Open “Exchange Management Console”.
- Expand “Server Configuration”>Select “Mailbox” .
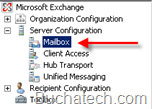
- You should now see the “Database Management” tab in the lower center console.
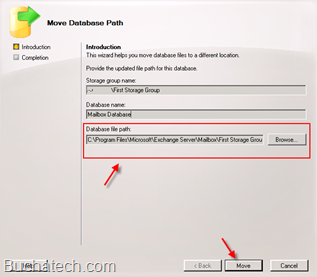
- Right click on each of the Storage groups and click “Move Database Path”.
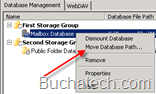
- Record the “Database file paths”.
- Go to your new drive that you are going to move the store to and create a folder to move it to. I recommend that you create a similar path (folder structure) to the folder you are moving your store to. EXAMPLE: %newdrive%\Microsoft\Exchange Server\Mailbox\First Storage Group\.
- No go back into “Exchange Management Console”>”Server Configuration”>“Mailbox”.
- In the lower center console right click on the Storage group you want to move and click “Move Database Path”
- Click the browse button and select the path to the folder you created in the previous step.
- Once you have selected the path click the “Move” button.