I will be co-presenting an AKS Learn Live this month with Microsoft Principal Cloud Advocate Steven Murawski on “Taking Your Intelligent App Global with AKS”!. It will be moderating by Principal Product Manager Brian Redmond!
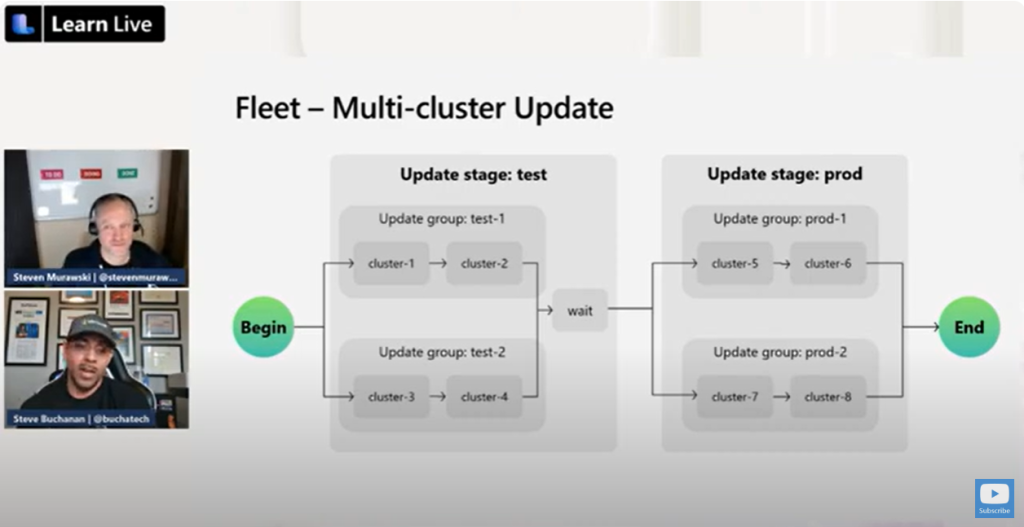
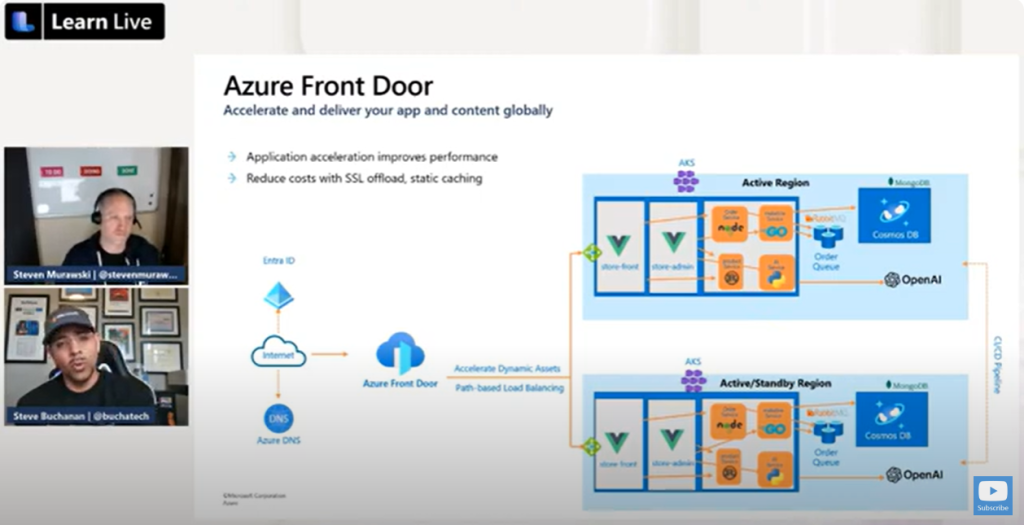
We will touch on using Azure Front Door and Fleet Manager. Description of the session:
“Once we have our intelligent application running, it’s time to make it scale. Using globally-scalable services like Azure CosmosDB and Azure Front Door, along with AKS Fleet Manager, we can take bring our intelligent apps closer to their consumers, while providing a consistent operating experience for the developers and operations personnel responsible for the service.”
You don’t want to miss this one!
Register here:
https://lnkd.in/gbJXzWSJ
__Update__
If you missed the session, no worries. You can access the lab here:
https://moaw.dev/workshop/?src=gh:smurawski/moaw/learn_live_spring_2024/workshops/aks_global_scale/
You can watch the recording of it here: